AWS News Blog
AWS CloudHSM Update
I’d like to give you a quick update on AWS CloudHSM.
First, the “HSM” is short for Hardware Security Module. As I noted in my earlier blog post:
An HSM is a piece of hardware — a dedicated appliance that provides secure key storage and a set of cryptographic operations within a tamper-resistant enclosure. You can store your keys within an HSM and use them to encrypt and decrypt data while keeping them safe and sound and under your full control. You are the only one with access to the keys stored in an HSM.
The AWS CloudHSM brings this service to the cloud. Each of your CloudHSM’s has an IP address within a Virtual Private Cloud (VPC).
Good News
We are expanding the CloudHSM footprint, while also making it easier for you to start using it. Our partner SafeNet has released some new encryption tools and is also publishing integration information for popular third-party applications.
CloudHSM Expansion
Effective immediately, CloudHSM is available in two additional AWS Regions. Here’s the complete list (the last two are new):
- US East (Northern Virginia)
- EU (Ireland)
- US West (Oregon)
- Asia Pacific (Sydney)
Getting Started
We have published a new CloudFormation template to help you get started with CloudHSM. The template prompts you for your EC2 key pair and asks you to choose three Availability Zones:
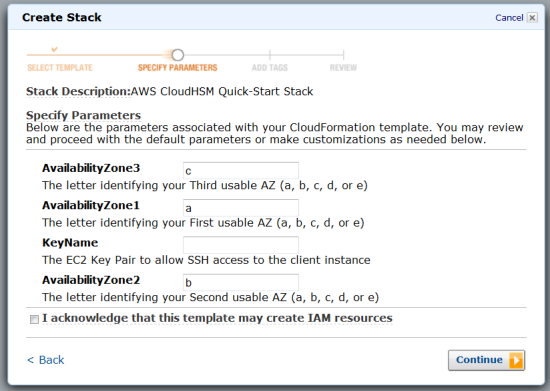
The template creates the following AWS resources:
- A Virtual Private Cloud (VPC).
- A single public subnet.
- One private subnet for each AZ in the Region.
- An IAM role that’s needed for the CloudHSM provisioning process.
- A security group that allows SSH access to the public subnet from the Internet.
- A security group that allows SSH and NTLS access to the private subnet from the public subnet.
- A 64-bit m1.small EC2 instance in the public subnet, booted from the Amazon Linux AMI with the SafeNet client software already installed.
- an Elastic IP address for the EC2 instance.
- IAM credentials used to send an SNS notification of your stack’s configuration to the CloudHSM team. The team will use this information to connect your CloudHSM to the proper VPC subnet and IAM role.
Here’s how these AWS resources fit together:
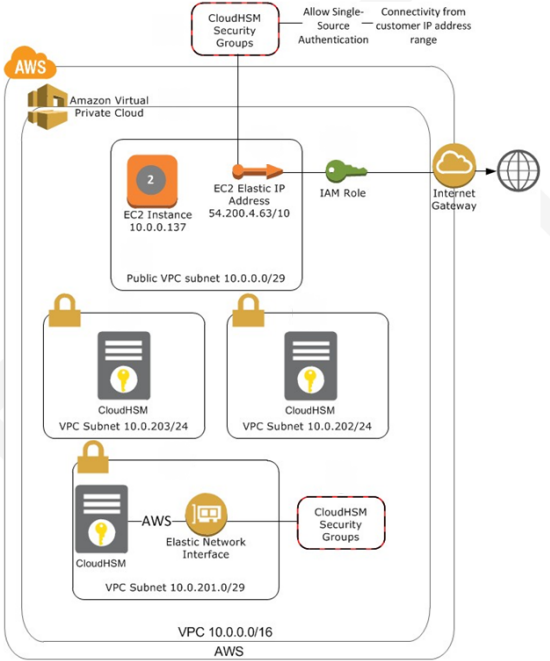
News From SafeNet
Our partner SafeNet has released a pair of new products that take advantage of the CloudHSM. Both of the products are available in the AWS Marketplace:
ProtectV (available in 5, 25, and 100 node configurations) is designed to provide isolation of data and separation of duties. It encrypts entire EC2 instances and the attached storage volumes. The ProtectV StartGuard provides pre-boot authorization to regulate the launching of EC2 instances.
Virtual KeySecure (available on a monthly or hourly basis) centralizes key management for instances secured by ProtectV, as well as for other cloud-based applications. Virtual KeySecure help organizations to ownership of their encryption keys at all times by hardening the appliance OS and encrypting the entire virtual appliance.
The folks at SafeNet have also released step-by-step configuration instructions that will walk you through the process of integrating CloudHSM with a number of third-party applications including Oracle Database, Microsoft SQL Server, and the Apache Web Server. You can find this information in the new Integrating Third-Party Applications with CloudHSM section of the CloudHSM Getting Started Guide.
— Jeff;