AWS News Blog
Custom SSL Domain Names and Root Domain Hosting for Amazon CloudFront
I am happy to announce that Amazon CloudFront now supports a pair of frequently requested features: support for custom SSL certificates and the ability to point the root of your website to a CloudFront distribution. With support for both of these features in place, it is now even easier for you to deliver your entire website via CloudFronts global network of edge locations. This includes the dynamic content, static objects, and the secured portions of your website or application.
Custom SSL Certificates
When a user requests content from a web site using the HTTPS protocol, the web server encrypts the data with a digital certificate before sending it along. The information in the certificate identifies the source of the content and also supplies the decryption key. Protecting content in this way increases user confidence and trust in the site.
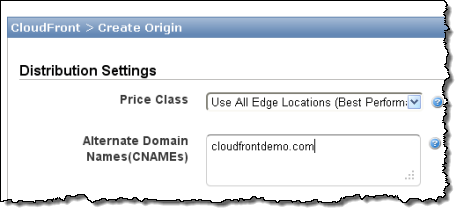
When you create a CloudFront distribution, you receive a unique domain name for your distribution e.g. d123.cloudfront.net. You can use this domain name directly in your URLs, or create a CNAME to something your viewers are familiar with or that represents your brand e.g. www.mysite.com. However, until today you couldnt use this CNAME to deliver your content over HTTPS as CloudFront edge servers didnt have the SSL certificate for your domain to hand out to the browsers. Thats changing today!
You can now upload a SSL certificate and instruct CloudFront to use it when handling HTTPS requests for a particular CloudFront distribution.
To get started, you need to request an invitation on our web site. As soon as your request is approved, you can upload your SSL certificate and use the AWS Management Console to associate it with your distribution. Here’s what you need to do:
- Purchase a Certificate from a Recognized Certificate Authority. Your certificate must be in X.509 PEM format, and must include a certificate chain. CloudFront supports many types of certificates including domain validated certificates, extended validation (EV) certificates, high assurance certificates, wildcard certificates (*.example.com), and subject alternative name (SAN) certificates (example.com and example.net).
- Upload the Certificate to Your AWS Account. Use the IAM CLI to upload the certificate to your AWS account as follows:
iam-servercertupload -s www.cloudfrontdemo.com -k privatekey.txt -c certchain.txt -b publickey.txt -p /cloudfront -v
Note that you must include the -p (path) option to indicate that the certificate will be used with CloudFront. Read the iam-servercertupload documentation for more information.
- Map Your Domain Name to Your Distribution. Create a CNAME record in your site’s DNS record set to map the domain or sub-domain to the distribution’s domain name. You must also inform CloudFront that the distribution is associated with the domain:
- Associate the Certificate with the Distribution:
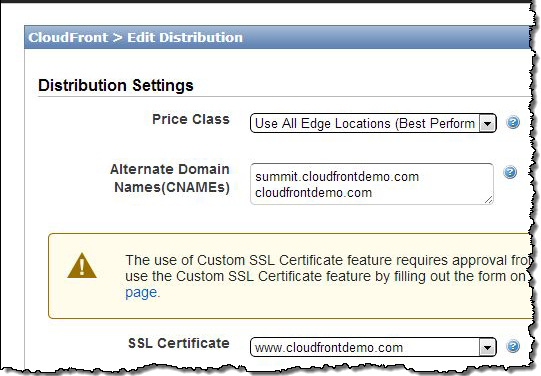
And that’s all it takes!
When your viewers download your content from CloudFront over an SSL connection, their SSL connection will terminate at a CloudFront edge location. This will remove some of the burden of SSL encryption from your origin server. You can also configure CloudFront to use an HTTPS connection for origin fetches, resulting in end-to-end encryption all the way from your origin to your users.
We charge a fixed monthly fee for each custom SSL certificate, with pricing pro-rated to each hour of usage. More information on pricing for the use of SSL certificates is available on the CloudFront pricing page.
Detailed documentation on the entire process is available in the CloudFront Developer Guide.
Root Domain Hosting
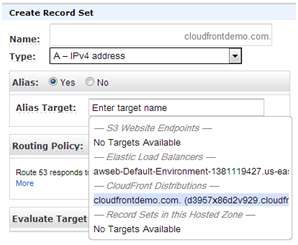
You can now use Route 53 (the AWS Domain Name Service) to configure an Alias (A) record that maps the apex or root (e.g. “cloudfront.com”) of your domain to a CloudFront distribution.
Once configured, Route 53 will respond to each request with the IP address(es) of the CloudFront distribution. This will allow visitors to easily and reliably access your web site even if they don’t specify the customary “www” prefix.
Here’s all you need to do:
Route 53 does not charge for queries to Alias records that are mapped to a CloudFront distribution. You can now use Route 53’s Alias records instead of CNAME records for all domain entries that point to CloudFront distributions. Read the Route 53 Developer Guide to learn more about this new feature.
— Jeff, with lots of help from Nihar Bihani;
Update: Some of you have expressed surprise at the price tag for the use of SSL certificates with CloudFront. With this custom SSL certificate feature, each certificate requires one or more dedicated IP addresses at each of our 40 CloudFront locations. This lets us give customers great performance (using all of our edge locations), great security (using a dedicated cert that isnt shared with anyone else) and great availability (no limitations as to which clients or browsers are supported). As with any other CloudFront feature, there are no up-front fees or professional services needed for setup. Plus, we arent charging anything extra for dynamic content, which makes it a great choice for customers who want to deliver an entire website (both static and dynamic content) in a secure manner.