AWS News Blog
Prepare for the OWASP Top 10 Web Application Vulnerabilities Using AWS WAF and Our New White Paper
|
|
Are you aware of the Open Web Application Security Project (OWASP) and the work that they do to improve the security of web applications? Among many other things, they publish a list of the 10 most critical application security flaws, known as the OWASP Top 10. The release candidate for the 2017 version contains a consensus view of common vulnerabilities often found in web sites and web applications.
AWS Web Application Firewall, as I described in my blog post, New – AWS WAF, helps to protect your application from application-layer attacks such as SQL injection and cross-site scripting. You can create custom rules to define the types of traffic that are accepted or rejected.
Our new white paper, Use AWS WAF to Mitigate OWASP’s Top 10 Web Application Vulnerabilities, shows you how to put AWS WAF to use. Going far beyond a simple recommendation to “use WAF,” it includes detailed, concrete mitigation strategies and implementation details for the most important items in the OWASP Top 10 (formally known as A1 through A10):
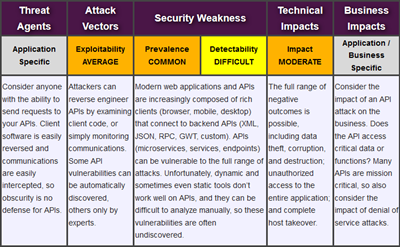 A1 – Injection.
A1 – Injection.- A2 – Broken Authentication and Session Management.
- A3 – Cross-Site Scripting (XSS).
- A4 – Broken Access Control.
- A5 – Security Misconfiguration.
- A6 – Sensitive Data Exposure.
- A7 – Insufficient Attack Protection.
- A8 – Cross-Site Request Forgery (CSRF).
- A9 – Using Components with Known Vulnerabilities.
- A10 – Underprotected APIs.
Download Today
The white paper provides background and context for each vulnerability, and then shows you how to create WAF rules to identify and block them. It also provides some defense-in-depth recommendations, including a very cool suggestion to use Lambda@Edge to prevalidate the parameters supplied to HTTP requests.
The white paper links to a companion AWS CloudFormation template that creates a Web ACL, along with the recommended condition types and rules. You can use this template as a starting point for your own work, adding more condition types and rules as desired.
Attend our Webinar
If you would like to learn more about the topics discussed in this new white paper, please plan to attend our upcoming webinar, Secure Your Applications with AWS Web Application Firewall (WAF) and AWS Shield. On July 12, 2017, my colleagues Jeffrey Lyon and Sundar Jayashekar will show you how to secure your web applications and how to defend against the most common Layer 7 attacks.
— Jeff;
Modified 2/11/2021 – In an effort to ensure a great experience, expired links in this post have been updated or removed from the original post.

